computer technologies and their subtopics
Have You Known That About Trojan Horse Malwares Before 2025?
"Trojan Horse Malware: The Silent Intruder Hiding in Plain Sight"

🧠 1. Introduction to Trojan Horse Malware
- What is malware?a malware is a short term for saying about a malicious software which codes are written for theft files from other person's computers or bug their system softwares so that couldn't get access to their own PC or theft by black hat hackers(cyber criminals).
- what is a trojan horse in computing?in computing , it is a type of files which may apper all correct to the user or for the operating system
- origin of the term "trojan horse"the term "trojan horses" has came out from the greek mythology. when the trojan war were having place in the history, the greeks has gifted a huge wooden cage horse to their enemies and left that out in front outside of their doors.but the fact that that cage was not emepty. therewere, some soldiers inside it in the night they came out and and became the reason of troy's downfall.🧠 In short: It's all about deception and hidden danger — both in the myth and in malwar
- how trojans are differ from viruses and worms?
- how trojans differ from viruses and worms?trojans threats you via showing themeselves as ethically correct or without the bugs and once you gave them some necessary permissions they theif your data.viruses wants user action to spread through his transferingor receiving files and worms don't need user's action for spreading out in whole OS once they enter.
🕵️♀️ 2. How Trojan Horses Work
- Basic functioning and infection method: a trojan horses shows itself as an ethically correct file without any flows but holds a suspicious set of codes to steal on users PC.it looks perfectly working for user's niche but the hidden codes secretly theifs other files and the main thing is they don't shows any suspicious signs while running in background without let the user know.
- Disguise and deception tactics:trojans are masters of camouflage they come infront of you with the mask of some popular softwares, games, seem as an important file
- Payload delivery and activation
- Remote access and command/control mechanisms
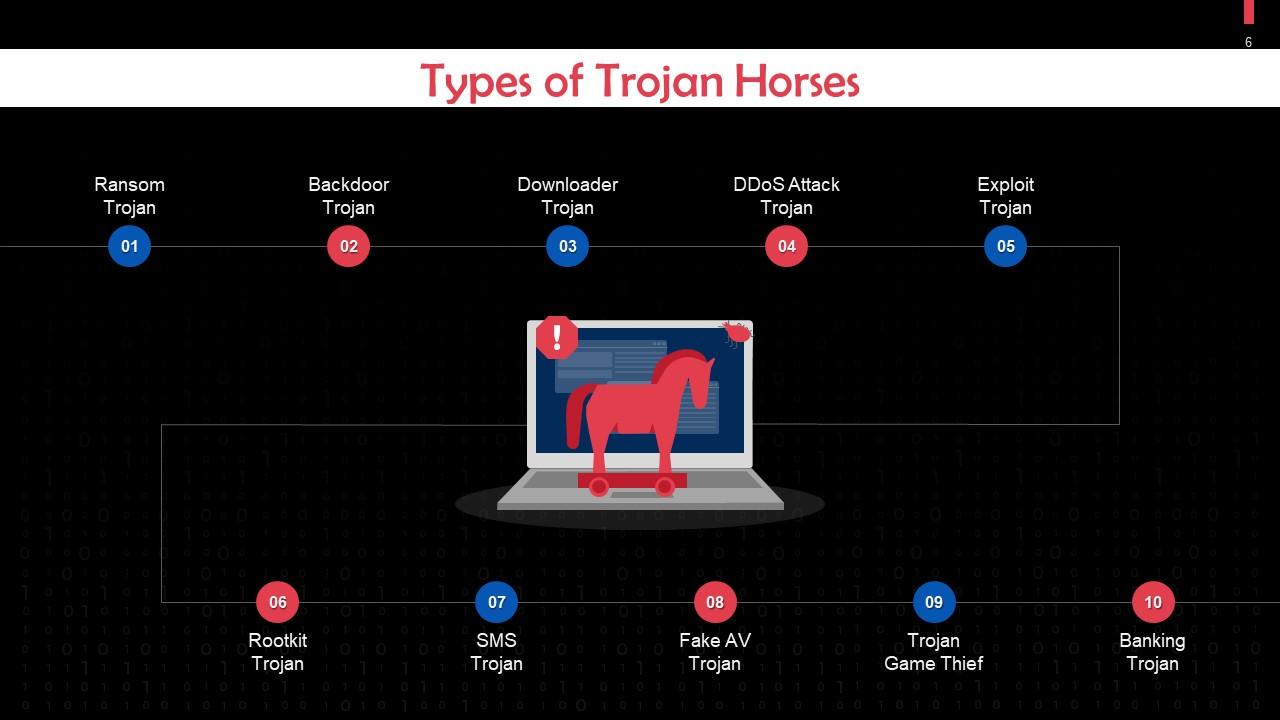
💣 3. Types of Trojan Horse Malware
- Backdoor Trojans – Remote control access
- Downloader Trojans –fetches other malicious softwares.
- Banking Trojans –using to theft on/steal from banking credentials of the user.
- Ransom Trojans – encrypt files for ransom.
- Spy Trojans –design/embedded to spy on user via records(mic) or cam(webcam) or through recording of the user's screen.
- Rootkit Trojans –hide another malwares in user's OS.
- DDoS Trojans –Launch distributed denial-of-service attacks
- SMS Trojans –Common in mobile devices (especially Android)
🧬 4. Infection Vectors
- Email attachments and phishing links
- Malicious websites or unwanted pop-ups
- Malicious websites or pop-ups
- Cracked software and pirated media
- Social engineering techniques
🧱 5. Real-World Examples of Trojan Horses
- Zeus Trojan (banking) banking trojan+keylogger is it's type.2007 was the year it was detective but still active till now in a evolvivg state/forms targeted for windows PCs but later adapted itself for the mobiles too.it's primary goal is to steal banking credentials/innformation, credit card data and cryptocurrency wallets.
- Emotet (modular Trojan) it was a banking malware which was emerged in 2014 but later emerged itself as a malvare delivery service who spread these malwares via phishing emails and malicious links attachments.
- trickBot similar to the emotet but where emotet acts like a s a gateway for other malware like ransomware, adware and viruses. but the trickbots mainly focuses on financial threats.
- Remote Access Trojans (RATs) like njRAT or DarkComet
- Mobile Trojans like Android.FakeApp
🔍 6. Signs You May Be Infected
- unknown actions : you detected in your computer which didn't made by you and even when you were inactive.
- you will find: some unknown src files or apps and any other kind of media.
- unwanted pop-ups: which is unusual for you.
- slow downs: your computer performing speed.
- aditionally,you'll find out changes in your system settings like homepage or firewall.
- generally, these all are the signs of that your PC has infected by trojan malware.

🛡️ 7. Prevention and Protection
- don't use: similiar features of premium apps with free apps like instagram with instagram lite and so on. they may apper good but could harm you more than you think.specially, it is not case all about money theft you privicy matters more than the money.
- always update your system's softwares.
- use strong passwords and multi-leval authentication while performing the tasks like login or signing in.
- be cautious with download and also read that how do they use your data.ex- chatgpt use your data for train their AI model.
- don't click on every thing you see on the internet.
- add on firewall and good reputable softwares in your system.
🧰 8. Detection and Removal
- use antivirus softwares for scanning and detecting these kind of malwares.like bitdefender, norton and malwarebytes.
- removeevery malicious files or programs.
- don't click those files which is sended by a stranger like src or even photos or stickers too.
- have a eye on your systems activities.
📱 9. Trojan Horses on Mobile Devices
- disguise itself as an authentic/legit app or software trojans copy the legal apps like games , editing softwares and much more often spread through third-party apps.
- famous/common attack methods are sms trojans for theft the credentials of the user and malicious permissions for the apps.
- primary risks data theft, premium sms scams and hijacking the user's device.
⚖️ 10. Legal and Ethical Implications
- for good purposes: if it is bad,there is also some good use of trojan horses by government.
- like they uses these kind of malicious programs for search on the user's history that could help them to find out that the person is guilt or not.
🧑💻 11. Trojan Horses and Cybersecurity Trends
- AI powered trojan horse malwares new trojan malwares is making themselves as an AI powered trojans or programs so that they could easily settle in user's system and mimic user behaviour. and the dangerous thing is they could easily adaptin your PC.
- in simple way, they can do their work or pulling files from your device whenever you usually deactive on the PC. and also could hide them when it's your activation time on your pc with the help of spied / collected data frrom your system via AI integrated program in their developing software.
- not only PCs nowadays, trojans are not just limited to PCs but can integrage with all smart devices like mobiles,tables and now built in with tachnologies like cloud and AI. they could integrete themselves with social engineering too and with the help of AI they could imitate the user behaviour and act like the user action so that the malware detecting softwares could not detect them.
- suppliers and their supply chain attacksCybercriminals are embedding Trojan malware into legitimate software distributed through trusted vendors in supply chain attacks.trojan can spread through networks and links ,harm/steal your data and could make the backdoors or path to upcoming malwares like this for future.
- ransomware-trojan hybrid ransomwares locks the device for user's use and and trojan infects the systems data or could steal some special credentials.
- cloud-based trojan cloud computing systems are also vulnerable so that trojans are now enter more easily in user's systems.



